According to statistics — the more enterprises transfer their operations to digital reality, the more cybersecurity risks appear. According to data collected by Microsoft, nearly 80% of nation-state attackers targeted government agencies, think tanks, and other non-government organizations.
What would you do? Do you and your organization have a response plan?
We think we know the answer — according to an IBM report, only 26% of firms have a well-defined security response plan for data breaches and other types of cyberattacks. This article will discuss what a cybersecurity incident response plan is and how it will benefit you. We'll share a step-by-step guide to creating an incident response plan and provide additional tips to help you get started.
In this article:
What is the incident response?
Incident response (IR) is a systematic approach that helps IT departments be ready to deal with incidents such as service interruption, organizational security breaches, or cyber-attacks and create a proper plan of action.
Due to the current situation where businesses have had to move to remote work, no organization is completely immune from IT incidents, especially security-related incidents. The consequences of security incidents are almost always catastrophic, as they involve data destruction, breach of confidentiality, and significant damage to an organization's productivity and financial health. It isn't easy to return to the previous state after such incidents. However, with an effective IR plan in place, it is possible to respond to such situations more effectively and restore normalcy more quickly. Ponemon's Data Breach Cost Report confirms that organizations with a robust IR plan have been able to reduce security breach costs by an average of $2 million.
Therefore, organizations should, as a matter of priority, develop a clear IR action plan and develop an appropriate process that will indicate what the organization considers as an incident, form a team of specialists responsible for responding to incidents, and assign appropriate roles to each, and train them as soon as possible.

By the way...
Do you know what are top security threats this year?
Cybercrimes caused more than $1 trillion of annual loses. In this article, we will tell you what hackers are targeting. Check if you're protected.
Let's seeWhy you need an incident response plan
The top reasons why every organization needs a well-documented and regularly updated cybersecurity incident response plan.
1. You will be prepared to fight cyber attacks
With a response plan, you and your team will know what needs to be done. In this case, everyone will have a documented role and responsibility. You will not need to give additional instructions to your team, so there is no loss of time or interruptions in communication.
2. You will follow the rules
In the event of a security breach, you must comply with many requirements, such as informing stakeholders and reporting the incident to the authorities. And a response plan will help you track and strictly adhere to these requirements. For example, the GDPR consumer data protection law requires you to report a security event within 72 hours of its occurrence, and the PCI DSS financial information security standard requires you to have an incident response plan and review it at least once a year.
3. You won't have to rely on special incident response measures
A cybersecurity incident response plan is a written document that clearly outlines the steps you and your employees should take when a security breach is discovered. The company's management approves, so you do not have to improvise. Agree that a pre-prepared answer is more effective than a spontaneous and chaotic one.
Steps of creating the incident response process
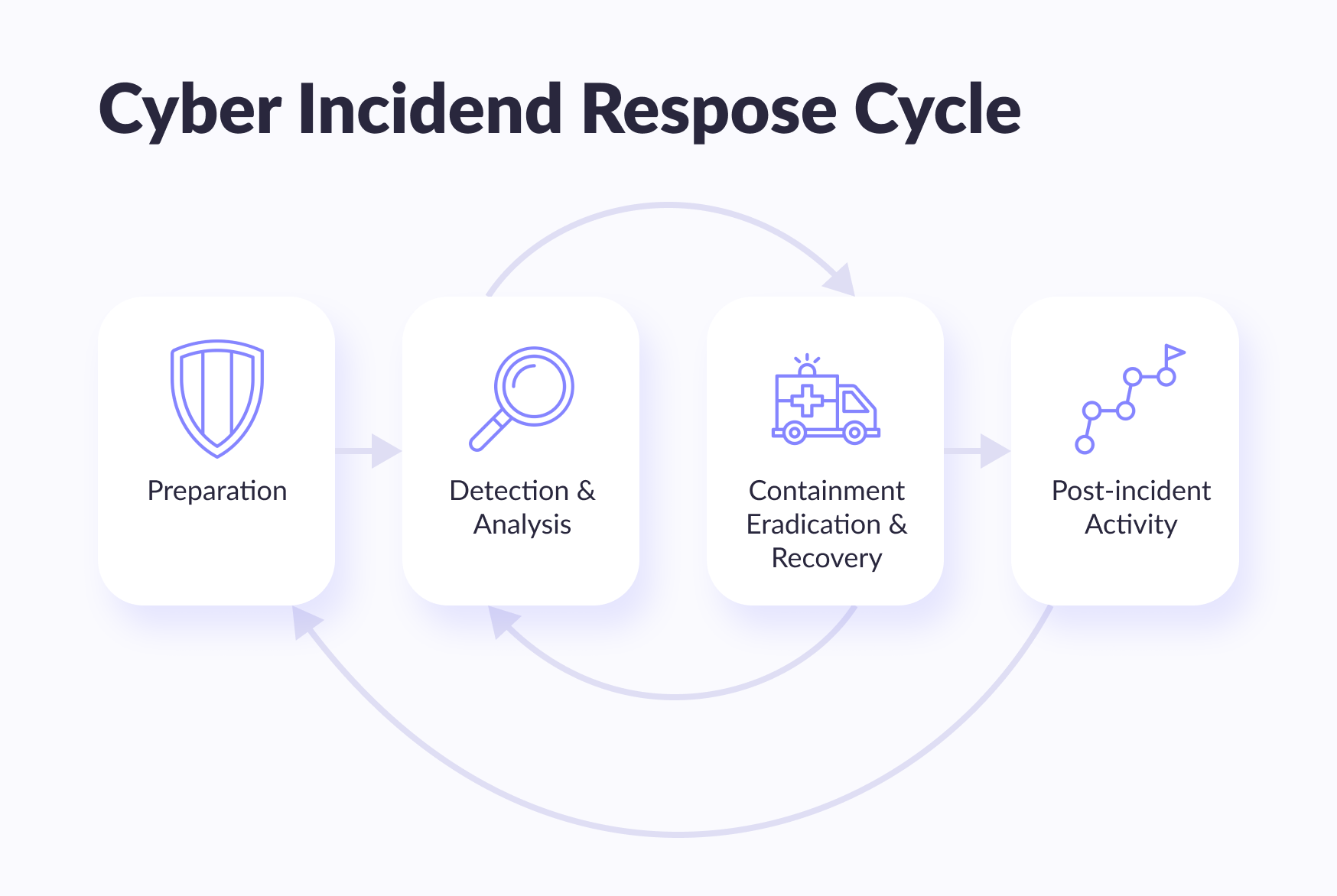
The way an organization deals with incident response has a significant effect on the impact of an incident. Typically, the incident response begins with developing an IR plan based on the necessities and functioning of the organization and the distribution of roles and liabilities to the incident response team members. The various security incident response steps offered by the National Institute of Standards and Technology (NIST) (USA) are listed below.
1. Preparation
Preparation is the most important step in incident response. Developing a strategy, documenting it, forming an incident response team, assigning roles and responsibilities, organizing proper communication and training, and preparing the necessary software and hardware are all part of an incident response plan and preparation for resolving a security breach.
2. Detection and analysis
This phase is where the actual incident response is performed, starting with finding and reporting security incidents. This raises the question of who reports the incident and how.
All members of the organization should be familiar with the IR plan in place and immediately report any suspicion of a security breach. It is important to share the IR plan with clients so that they keep their fingers on the pulse. Both employees and customers should report security issues in their work environment. Below are a number of scenarios where the problem should not be ignored but should be reported as soon as possible in order to resolve it promptly.
- Customers report security issues through the organization's help desk channels;
- Threats to customer data due to security issues found within the organization;
- Security alerts from various intrusion detection systems and monitoring tools;
- Email messages that may contain viruses;
- Detect malware on any device in your organization.
When employees encounter security incidents, they should immediately report them to the IR team. An organization should use a variety of ways to detect security incidents, such as self-service portal web forms, emails, chats, phone calls, digital collaboration workspaces including Microsoft Teams, and more. All this must be clearly defined in the IR plan and published to employees and clients.
NIST suggests five steps for the discovery and analysis phase:
- Detecting the very first signs of a security incident;
- Analysis of signs to distinguish a real threat from a false alarm;
- Documentation of the incident, recording all the facts and the appropriate response procedures that should be applied to resolve the problem;
- Prioritize an incident based on impact analysis, considering its business and privacy implications and the time and effort required to recover;
- Notifying teams and individuals involved by the IR team, explaining the IR plan and the necessary actions for a quick recovery.

More on the topic
Types of cybercrimes and how to prevent them
The share of leaks, breaches and targeted attacks is growing. Find out how to protect yourself in this article. Based on a real expertise.
Find out more3. Containment, liquidation, and recovery
Containment refers to actions to bring an incident under control as soon as possible and block it to prevent further damage. This requires pinpointing the systems under attack and isolating the effects of containment, elimination, and recovery within an IR plan. To resolve the issue, you can use effective incident management tools and use the solutions offered in the support knowledge base articles. A recovery strategy is required for a security incident to be considered closed. This phase also includes checking affected systems and returning them to normal functioning.
All these strategies should be based on criteria such as the severity of the security incident, the state of the systems affected, the impact on the business, the logging of evidence and all information about the incident, and the tools and resources needed to coordinate the strategy.
4. Evaluation (after analyzing the incident)
After each incident, a review meeting should be held with the IR team, management of the organization, and each individual involved in the incident to draw appropriate conclusions and review the effectiveness of the IR plan and strategies at each stage. Here are a few things to consider during the evaluation phase:
- The root cause of the incident and where it occurred;
- Possibility of preventing an incident earlier;
- The effectiveness of the IR plan and the work of the IR team;
- The effectiveness of strategies at every stage;
- Tasks that could go unnoticed;
- Any steps that could be more effective if done differently;
- Threat detection to prevent similar incidents in the future.
In addition to understanding how to respond to incidents, it is also important to understand that an effective IR process cannot be implemented without the appropriate tools and tools. Organizations often lack the right skills and need to outsource IR. Either way, effective incident response requires a comprehensive incident management tool that minimizes damage and downtime.
Additional advice for rapid incident response
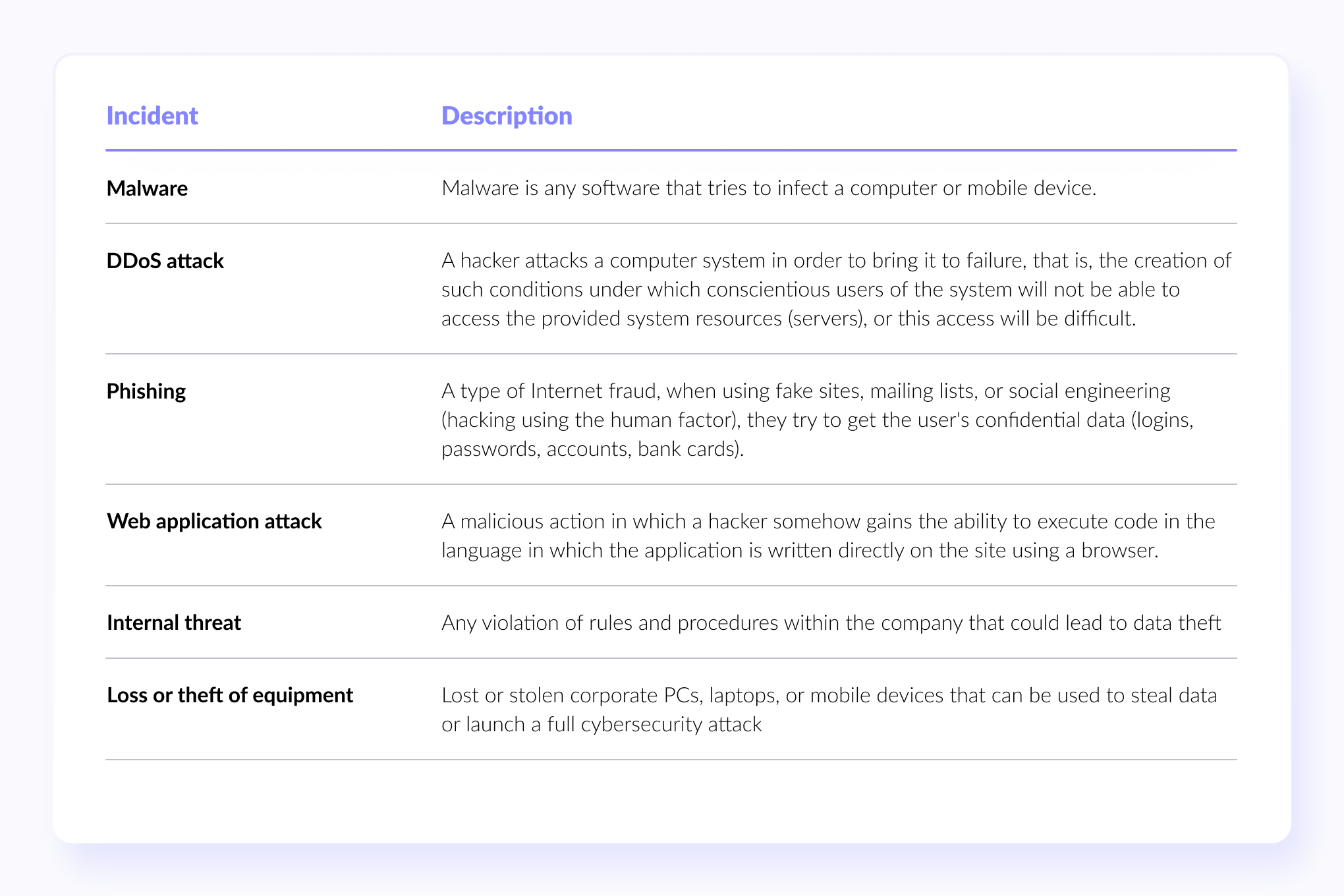
1. Document the common types of security incidents
To get started, create a document listing potential threats to your business to help you prepare different strategies for responding to different types of cyber incidents. Below we give an example of an incident table that includes the most common issues with every business.
2. Prioritize security incidents based on their severity
Security incidents vary in size and severity. A corrupted file on an employee's laptop can be considered less of a priority compared to a DDoS attack that can take down an entire site. Determine the severity of each security incident to decide if it should be resolved first.
So, evaluate whether the incident affects your data (makes it inaccessible, steals, or causes it to be lost) or your ability to serve customers or perform operations. Any incident that impacts data security and operational security should be dealt with as a matter of priority.
3. Create an Incident Response Flowchart outlining required actions
The Incident Response Plan will define the steps you must take to contain an attack. Lay out your plan in a flowchart so your team can quickly understand which mitigation path to take.
Specify who is responsible for completing each step mentioned in your flowchart. Distribute clear and non-conflicting responsibilities among your employees so that there are no clashes or unnecessary disputes.
Use the Responsible, Accountable, Consulted, and Informed (RACI) matrix to indicate who should be responsible, accountable, consulted, or only informed about the various incident response steps. It can be as small as one person. For example, your security manager will be responsible for keeping records of incidents, being in charge of technical operations, consulting on post-incident reporting, and informing on overall coordination and interaction with regulators.
4. Test drive and train your employees
An incident response program alone is not enough. You need to test its effectiveness by conducting simulation exercises that will also train your employees in their role in security incident management. Here is an effective red and blue team exercise you can do as a model.

Red Teaming (red team attack) is a complex simulation of real attacks to assess the systems' cybersecurity. The Red Team is a group of pentesters (professionals who perform a penetration test on a system). They can be hired from outside or employees of your organization, but in all cases, their role is the same — to imitate the actions of intruders and try to penetrate your system.
Along with the "red teams" in cybersecurity, there are a number of others. For example, the Blue Team works together with the Red Team, but its activities are aimed to improve the security of the system's infrastructure from the inside. The Purple Team is the link, assisting the other two teams develop offensive strategies and defensive measures. However, red timing is one of the least understood methods of cybersecurity management, and many organizations remain reluctant to adopt this practice.
5. Update your incident response plan regularly
Update your plan regularly to keep up with changes in the threat landscape or to include any new security measures you've recently taken. At least once a year, review your response activities and work to reduce the time you spend containing and recovering from incidents.
Use the information gathered from previous security incidents and simulation exercises to identify improvement opportunities and implement new controls for your security incident response plan (for example, be sure to look for steps that can be automated).
And finally, use special software to help you detect and eliminate security threats more effectively. They allow business operations to continue even when incident response activities run in the background.
Here are some of them:
- Antivirus software;
- Endpoint Security Software;
- Network security software;
- Network monitoring software;
- SIEM;
- Data backup software;
- Business Continuity Software.

We thought you might need it
Zero trust security
Have you ever tried to treat your system as if it already was compromised? Try a security model that offers better access control, and faster detection of threats, and is based on a holistic approach. P.S. This article is recommended by our CTO.
Tell me moreConclusion
Remember that developing a cybersecurity incident response plan is not a one-time event. Unfortunately, without regular incident response training and drills, including real-time cyber-attack scenarios, organizations, and their IT security teams can suddenly find that hackers who change their attack strategies and malware selection are not up to the task. What worked in the past may not work tomorrow. A good security incident response plan should be a living document that keeps up with the rapidly changing threat landscape.





















