- What Is Zero Trust?
- Why Is Zero Trust Important?
- What Are the Differences Between Zero Trust Access (ZTA) and Zero Trust Network Architecture (ZTNA)?
- Zero Trust Core Principles
- Challenges in Implementing Zero Trust
- Five Steps to Zero Trust Implementation
- Zero Trust Best Practices
- Need Professional Help?
- Conclusion
Which barrier do you think is the most critical for enterprises while migrating to cloud technology? In a PwC survey, 63% of the participants reported network security as their most critical concern. Yet, migrating your organization's network to the cloud is inevitable, as the estimated global cloud computing market size by the end of 2023 will be $623.3 billion.
The zero trust security model has significantly changed the traditional data security approach and will be the gold standard of cloud-based network security architecture in the future. In contrast to the long-established “trust but verify” architecture of on-premise network deployments, the zero trust approach promotes and practices the “never trust, always verify” philosophy.
This article covers what zero trust security is and how to implement zero trust to secure your organization’s network infrastructure. You will also discover the challenges and best practices of zero trust implementation. Let’s quickly learn about zero trust architecture.
In This Article:
What Is Zero Trust?
Zero trust is a security architecture requiring all internal and external network users to go through continuous verification and validation before granting them access to the network resources. Continuous authentication is integrated within the zero trust network design, and the core philosophy, in a nutshell, is not to consider a network “trusted” without verification.
The dynamic nature of today’s multi-dimensional cloud network has seriously questioned the effectiveness of traditional security models and our perception of a trusted network.
Understanding cloud computing will help you see zero trust architecture's relevance. Cloud computing can have four major types: private, public, hybrid, and multi-cloud. It is unlikely that modern-day organizations will use one of these and ignore the others. Instead, businesses probably need to use all of them along with their internal private networks, leading to overlapping databases and networks.
As users access multiple networks simultaneously, there will be data exchanges between several networks and user devices. The possibility of data breaches will multiply in legacy systems because any devices validated as “trusted” may be infected with malware or similar threats and spread the malicious actor within the overlapping networks. This is why the system does not “assume” any device as “trusted” or safe and instead follows the zero trust policies to reduce risk through continuous authentication.
Why Is Zero Trust Important?
Now that we know the basic concepts of a zero trust network, let’s go through the importance of the zero trust model for mitigating cyber threats and protecting your enterprise resources from potential security breaches.
- Better access control. You will better control access management by validating the device and network attributes frequently in a zero trust network. You can do role-based segmentation of user groups and clearly define who will gain access to which areas of the network and storage.
- Faster detection. A zero trust policy will help you get continuous and almost instant updates on devices connecting to and disconnecting from your network. Thus, it will buy you more time to act and quarantine the affected areas to protect the enterprise network.
- Holistic view. You will repeatedly be checking the attributes and updated status of all the connected devices. As a result, you will always get a complete picture of your organization’s network.
So the importance of establishing a zero trust network to protect your critical data is clear as daylight. However, while discussing the zero trust architecture, many of us often get confused between zero trust access (ZTA) and zero trust network architecture. Although their purposes are essentially the same, these two terminologies are inherently different. Let’s check that out.
What Are the Differences Between Zero Trust Access (ZTA) and Zero Trust Network Architecture (ZTNA)?
ZTA focuses on controlling and managing who and what is allowed on your network. It manages both the presence and activities of a user by assigning role-based access permissions. With an ever-increasing number of IoT devices, ZTA is critical for managing IoT devices in a network. ZTA utilizes a minimum access policy to such devices so that they can only complete the assigned task and nothing more.
On the other hand, ZTNA focuses more on controlling access to applications instead of access to networks. It creates a gate-like barrier known as proxy points before network applications, which the devices and users must pass through to reach the application.
At this point, let’s get familiar with the core principles on which we will base our implementation of a zero trust network.

By the way...
What Is Legacy Code: Working With Legacy Code
Did you know that legacy code could also be dangerous to your business? Do not let it chain you on your way to market leadership
Let's seeZero Trust Core Principles
A zero trust architecture has three key principles to minimize the threat to your digital artifacts and sensitive data. Here are they:
Never trust without validation. The zero trust philosophy suggests that you must not assume a device or user as safe unless verified. Also, validating once is not sufficient; instead, it should be integrated as a continuous and iterative process. Thus, there is no place for implicit trust based on past authentication.
Always assume a breach. Keep in mind that any device or user can turn into a potential threat. So you must prepare ahead to segment or quarantine an attack surface of a network location in a short time.
Grant minimal access. A zero trust network adheres to the Principles of Least Privilege (PoLP), meaning you should always grant the least amount of secure access to any entity, which is just enough to carry out its assigned task.
Before we explore how to implement zero trust networks, there are several difficulties related to the implementation that we have to address.
Challenges in Implementing Zero Trust
Knowing the challenges of implementing a zero trust network architecture will help you prepare adequately. So, we have summarized some of the key challenges:
Complicated infrastructure. Infrastructure includes servers, network storage, firewalls, software applications, cloud platforms, databases, and so on. There may be a combination of on-premise, cloud, and hybrid solutions. Managing all of them together will require complicated hardware and software architecture.
High investment. Apart from the hardware and software sourcing cost, you will also need to factor in maintenance expenses, subscription charges, and human costs. When your current workforce is not familiar with the new security protocols, you will have to invest significantly in training and development.
Multiple software tools required. You will often be required to use and integrate multiple software tools to build a flexible zero trust system. There will be multiple segmentations and software-defined perimeters to limit your attack surface in the event of a potential attack.
Thus, the key challenges of implementing a zero trust network are related to the complexity and high investment requirement. Let’s now move on to the implementation steps.
Five Steps to Zero Trust Implementation
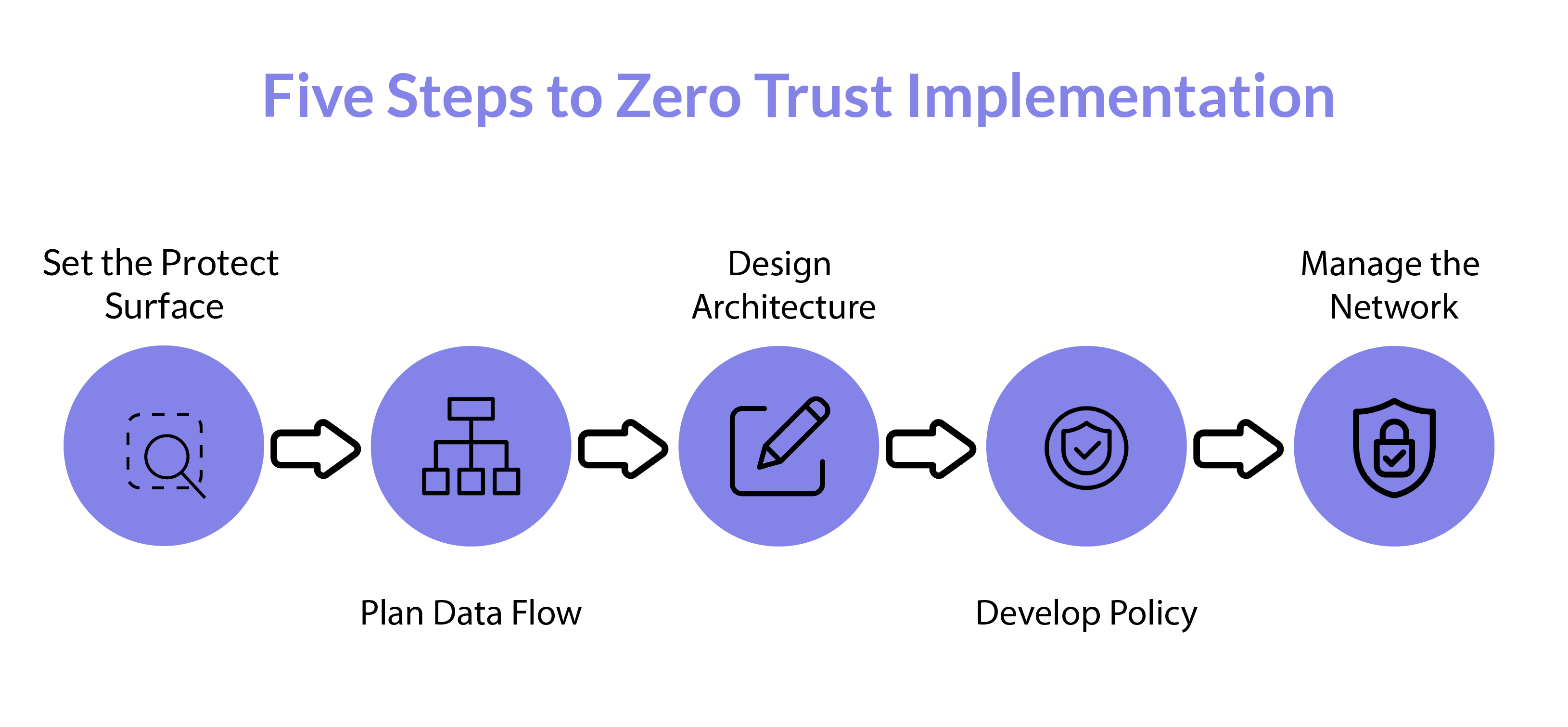 Implementing zero trust consists of five key steps, from defining the area to managing the network.
Implementing zero trust consists of five key steps, from defining the area to managing the network.
Set the Protect Surface
It is complicated and expensive to implement zero trust architecture. Therefore, you should define your protect surface clearly instead of aiming for a large network area. It denotes the specific components within the network that you will secure with this framework.
Examples of a protect surface include Data, Applications, Assets, and Services—abbreviated as DAAS.
Plan Data Flow
Mapping the flow of instructions and data will help get valuable insights into the overlapping networks. While mapping, you should include as many details and directions as possible related to the data exchange pathway. You can then plan the security measures accordingly.
Design Architecture
While designing the network architecture, you can begin with installing a next-generation firewall that will work as a segmentation gateway. That will prevent unauthorized access to the protected surface through micro-perimeters around it.
Afterward, you can update the segmentation gateway with additional layers of access control, such as installing layer-7 protection.

Important info
What Is A Good Application Architecture?
Architecture is literally the Atlas holding the success of your app. Do not let it fall.
Need itDevelop Policy
The next task is to prepare your policies using the Kipling method, which involves whitelisting the entities. You will need to specify answers to the following questions related to the trust network access:
- Who has access to resources?
- What internal applications should you use?
- When will it be accessed?
- Where is the destination of the data?
- Why does it require access?
- How is the trust network access taking place?
Manage the Network
Continuous monitoring, auditing, and maintaining a log for monitoring traffic will help you manage the network.
Now that we know how to implement zero trust, let's learn a few of the ideal practices of zero trust, as it will help us make the most efficient use of our resources.
Zero Trust Best Practices
Here is some practical advice based on best industry practices for your zero trust network:
- Use multifactor authentication (MFA). Always use MFA for stronger verification instead of relying only on passwords. It will significantly reduce the possibility of a network breach.
- Use updated devices. Always keep your network-connected devices up-to-date with the latest firmware and vendor-provided security patches. Also, replace the outdated devices with the latest ones.
- Always monitor. Make sure to monitor your network and device attributes consistently. No matter how updated your configurations are, there will always be loopholes if you do not keep an eye on them to maintain compliance.
Although the list of zero trust best practices is not conclusive, it will certainly help you get a solid idea about an efficient zero trust implementation.
Need Professional Help?
Due to the complexities and security threats involved in modern-day cloud computing, your IT team will eventually have to implement and maintain the zero trust architecture to safeguard your organization’s network resources. That said, the implementation involves dealing with challenges and investment requirements.
Professional assistance can make the journey smooth for you. Geniusee develops products and services for cybersecurity and provides consultancy and support for various clients and partners. They can be your ideal technical partner with expertise in the successful completion of 100+ projects related to FinTech, EdTech, AgroTech, real estate, tourism, automotive, and many more.
Conclusion
There is no fit-for-all approach businesses can adopt to deal with cyber threats. Each organization needs to find out its security loopholes and act accordingly. Implementing the zero trust network can ideally be your first step, and then you can integrate other measures to solidify your organization’s network.
Need a professional vision of services and products for cybersecurity? Ask the Geniusee specialists.





















