Data is a key driver behind every business decision, from how you engage customers to how you innovate. The more you use the cloud to grow and adapt, the higher the data protection and cloud security rank. Unfortunately, loss or breach of cloud data is not just a tech issue; it also threatens your reputation, financial status, and ability to continue growing your company in the future.
Cloud technology makes it easy to adapt. However, managing sensitive data and compliance becomes more challenging in mixed cloud scenarios. What does it mean? With stricter data laws like the GDPR being enforced globally, protecting data is essential, not just for compliance but to build trust.
Last year, data breaches increased by 6%, involving over 16.8 billion records, primarily due to poor password security and weaknesses in cloud storage. It costs an average of $5.17 million to resolve data breaches in cloud environments, which is more expensive than the $4.88 million post-breach cost elsewhere.
This article explores the key aspects of cloud data protection, providing details on threats, clarifying roles and responsibilities, and suggesting ways to enhance your security.
Why is cloud data protection strategically important?
Keeping data secure in cloud systems is now crucial for top-level business executives — it’s not just an IT concern. When there is a breach, cloud data is threatened, operations are disrupted, customer trust declines, and you could lose a lot of money.
Think about the 2019 Capital One incident, which exposed over 100 million customer records because of incorrect settings on the web application firewall and an unsecured storage bucket. There were consequences like closer regulation, lawsuits filed by many consumers, and long-term harm to the company’s image. This shows that misconfigured cloud systems can lead to high costs and long-term damage to a company’s reputation.
On the other hand, Dropbox uses cloud-based data security to gain business advantages. With practices like file encryption, strict safety protocols, and SOC 2 compliance, they have further strengthened customer trust. If cloud security is seen as a way to differentiate from competitors, it stops being merely a cost and becomes a strategic advantage.
Key issues in cloud environments
Effective cloud security depends on the most fragile part of your system. You must be aware of the risks that can threaten security, privacy, and compliance:
A misconfigured system
In 2023, Toyota had 2 million user records accessible for 10 years due to a misconfigured telemetry cloud.
Lesson: Security in the cloud depends on ongoing review and monitoring. When you don’t set up cloud services properly, you can lose or compromise data.
Shadow IT & third-party integrations
In 2019, Facebook experienced the theft of 540 million customer records due to insecure S3 buckets managed by some of its partners.
Lesson: Handling client data via third parties carries business risks. That’s why ensuring uniform data protection and privacy is essential for both companies and cloud providers.
Risks from insider threats
In 2021, Microsoft Power Apps left 38 million records vulnerable due to the application’s default settings.
Lesson: The default settings may not fully protect you. Proper identity and access management (IAM) helps secure your data and protect your cloud setup.
Varied governance structure
Using multiple cloud platforms increases the likelihood of issues. Without unified oversight of cloud security policies, businesses may fail to ensure the same level of data protection in all their environments.
Lesson: Strong, integrated security is a critical part of any cloud strategy.


Thank you for Subscription!
How to meet cloud security needs?
Protecting cloud data is as much about leadership as it is about engineering. Remember: you must coordinate responsibilities and integrate compliance into processes to improve cloud security. Here’s how:
1. Shared responsibility model
Many people run into trouble with cloud resources because they overlook or misunderstand the concept of shared responsibility. While the provider protects the cloud’s physical hardware, networks, and data centers, you have to secure data, oversee access, identity management, and verify application-level security.
If you depend on your cloud provider to protect your data without implementing your own safeguards, this can cause data breaches. Your company must clearly outline who is responsible for each stage of cloud data protection.
2. Management and access protocols
Another key aspect of cloud data security is controlling access to the data. When least privilege is enforced across all departments, teams, and applications, it helps reduce the risk of security problems resulting from employee mistakes.
A well-developed IAM program is essential when handling sensitive information or using multiple clouds. Managing security policies is simpler when platforms all use the same governance system.
3. Protecting data at rest and in transit
Data protection at rest and data in transit is included in basic cloud security rules. Beyond that, enterprises have to pay attention to how encryption keys are managed. Using bring your own key (BYOK) and hold your own key (HYOK), businesses are responsible for ensuring the security of their cloud data.
Implementing strong encryption ensures that customer data, personal data, and data stored in the cloud are protected, allowing businesses to comply with data privacy regulations and avoid costly breaches.
4. Data storage and adherence to guidelines
There are no global standards for data sovereignty laws. Companies should stay informed about where their data has moved, where it remains, and whether they follow regulations like GDPR, HIPAA, CCPA, and their local laws.
Selecting the correct cloud regions and understanding potential legal risks is crucial for all businesses that store data in the cloud, not just the legal team.
5. Having readiness for incident response
You must be prepared for a breach before an accident occurs. Having a comprehensive incident response program that involves legal, communication, and executive actions helps mitigate the impact of a security threat when it emerges.
Participate in breach simulations. And here’s why: a cloud data breach can damage the company's reputation, regulatory compliance, and harm operations, ultimately affecting business value and board confidence. Modern data cloud solutions require organizations to be ready for disruptions that align with their business continuity strategies.
KPIs and metrics that matter
To prioritize cloud data protection, you need detailed performance information. These KPIs are not just for security teams; they also help leaders understand business risks, compliance, and the ability to handle emergencies. Below are the key metrics that must be followed and reported to the board regularly:
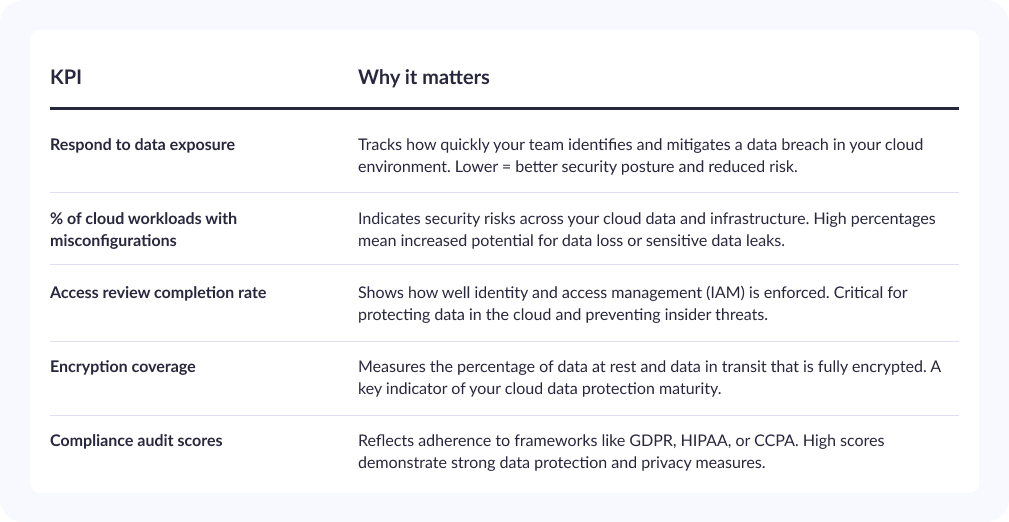
Things you should ask your teams
The initial step in achieving good cloud data protection is to ask the right questions. Below are 5 main questions leaders should consider when checking the maturity of their cloud security programs.
Is all sensitive data in the cloud being encrypted?
Encryption is always necessary. Ask your teams about whether they use reliable and robust encryption for all types of sensitive information. Apply key management solutions (BYOK or HYOK) to maintain control over your data and protect it against breaches.
Where does each provider hold our data?
Cloud data may be located in multiple jurisdictions and locations. If you are not sure where your cloud data is stored, you may run into unplanned data sovereignty risks or violate GDPR or HIPAA compliance standards.
When was the last review of access?
Breaches often occur due to outdated or unnecessary system permissions. Regularly check IAM configurations to ensure least-privilege access. Failing to review new rules can leave customer data vulnerable to risk and may lead to compliance failures.
How do we monitor and control third-party and vendor risks?
Having cloud services isn’t the only point you need to consider. The use of integrations, APIs, and tools from different providers increases the risk area. If shadow IT systems are not adequately verified or cloud systems are poorly managed, data may be exposed, especially with multi-cloud connections.
What process do we follow for responding to a breach in our SLA?
Speed matters the most when dealing with a data loss or a breach in cloud data. Leaders are responsible for establishing an organized incident response system with well-defined responsibilities for those in security, legal, and PR. So, what should you do? Check how quickly the company can detect and stop an incident.

More from our blog
Predictive analytics in education: from data to impact
Predictive analytics can reshape learning and drive real impact. Embrace smart insights — the future starts now!
Read moreStrategies for progress
Discussing cloud data protection now requires thinking about business strengths, reputation, and operational activities. To keep data safe in the cloud, take a look at the following steps:
1. Establish and maintain cross-functional cloud security rules
Enforcing cloud security is a team effort, not just a task for IT. Security policies should be developed and analyzed by the Legal, Compliance, Risk, and Product teams.
Create a centralized cloud data security program covering all business divisions.
Review the company’s strategy based on legal, operational, and reputational risks.
Choose a leader to ensure data readiness for auditors.
2. Use continuous compliance and monitoring tools
As your cloud environment evolves, your data protection system must adapt accordingly. Set up tools that can spot cloud data misconfigurations, policy issues, and any threats to your system instantly.
Have the system automatically scan for signs of data breaches and compliance violations.
Utilize AI systems designed to identify anomalies in real-time and prevent data loss quickly.
Watch for dangers introduced by changes made to your cloud provider by other teams.
3. Coordinate cloud security efforts with organizational goals
An effective cloud data security strategy should support both new product development and entering market expansion by reducing hurdles, not adding them.
Set up KPIs that relate cloud security status to the business’s key activities.
Ensure that the data security choices you make build client trust.
Pick security and protection tools that match your increasing data storage needs.
4. Ensure that the board is informed about the project
Losing data through the cloud, facing penalties for non-compliance with regulations, or experiencing public incidents can significantly impact a company's market valuation.
Add metrics on encryption, access control, and the company’s response to breaches in the report.
Discuss data security and privacy trends in reports to the board every quarter.
Add the management of cloud risks to the organization’s risk planning and strategy.
Conclusion
Strong cloud data protection is necessary for compliance, but it also helps a company pull ahead of competitors. With robust security, good governance, and effective data protection and privacy, your company can enhance operations, comply with evolving privacy regulations, and earn stakeholder trust.
Need support in protecting your cloud data?
At Geniusee, our team helps companies protect their data in the cloud, aligning with their business objectives. We offer cloud security posture management, data loss prevention, and compliance support to keep your systems resilient and audit-ready. Let’s team up to secure your data, protect your users, and manage upcoming projects. Contact us now.





















