Here, at Geniusee, we strive to provide our clients with the best services. That is why we’re improving our products and services and evolving in every possible way. We prefer real evidence, instead of bare words, so we never talk about something we can not prove.
Today, we’re thrilled to share with you amazing news: we received a certificate ISO 27001:2013.
In this article:
What is ISO 27001:2013?
We may describe ISO 27001:2013 as a way of life and thinking. It allows companies to enhance their security posture overall. Firstly, the C-levels go, leading the example in order to make changes genuinely effective.
If we make it official, ISO 27001:2013 is a standard by the International Organization of Standardization in the field of information security that requires organizations to provide and adopt ISMS or, in other words, information security management systems.
Security objectives of ISO 27001
ISO 27001 is designed to be a shield for three informational aspects:
- Confidentiality
- Integrity
- Availability
This means that information in the company that implements ISO 27001 should be authorized only for individuals or organizations that have a right to access and change it and should be available whenever they need it.
Why is ISO 27001 so important?
For Geniusee
ISO 27001 empowers companies with proven and effective approaches to protect sensitive data, internal and external information that gets into the company, clients’ and employees’ information, and ways to prevent leaks, data breaches, malicious insider activity, etc.
For Partners
You, as our client, may be sure now that all information that you trust us, all communication, and work results are as well secured as possible.
What is an ISMS?
Now, let’s find out what is ISMS and what are benefits for the company that uses it.
An information security management system is a systematically organized set of methods tailored to manage information within a company in order to make it secure. It refers to IT systems, company processes, and people, taking to account formal risk management of structures, approaches, and business processes.
Why do we need ISMS?
Any company that implements ISMS achieves four benefits that are pillars for further growth and development:
- Legal requirements compliance
- Competitive advantage achievement
- Cost reduction
- Organization improvement
How does ISO 27001 work
ISO 27001 is focused on protecting the information in a company and ensuring its availability, integrity, and confidentiality, all in accordance with regulatory requirements.
It allows solving some potential problems before they even take place in reality. It refers to risk assessment mostly, preventing data breaches, viruses, malicious software or “warms”, ransomware, etc, and to risk mitigation and risk treatment as instruments that allow averting threats issues.

By the way...
Critical cybersecurity breaches 2022
The annual losses from cybercrime in the world already amount to trillions of dollars even with serverless architecture.
Find out what to expectYet, the main point of ISO 27001 is security, its core is based on something more than that: risk management. The inner workings and philosophy of ISO 27001 are constant work and, maybe, we could even call it a fascinating adventure. Discovering risks, treating them systematically, implementing safeguards and threat intelligence… Sounds like a story about pirates or spies, doesn’t it?
Risk management and ISO 27001:2013
As we have already mentioned, risk management is a foundation of ISO 27001:2013. All information security management systems within a company should rely upon regular risk assessments. It allows companies to determine if they need to implement security measures, which security controls are necessary, and maintain them properly.
Clauses and controls
ISO 27001 has ten management system clauses that help support the performance and supervision of ISMS.
Clauses:
- Scope
- Normative references
- Terms and definitions
- Context
- Leadership
- Planning and risk management
- Support
- Operations
- Performance evaluation
- Improvement
ISO 27001 also has a list of controls and not all of them should necessarily be implemented. The risk assessment process conducted by the company should enlighten which controls the company needs to implement or exclude.
Controls:
- Information security policies
- Organization of information security
- Human resource security
- Asset management
- Access control
- Cryptography
- Physical and environmental security
- Operations security
- Communications security
- System acquisition, development, and maintenance
- Supplier relationships
- Information security incident management
- Information security aspects of business continuity management
- Compliance
How to achieve ISO 27001:2013 compliance?
Well, now the most interesting part. What does it take to implement ISO 27001?
The short answer is a lot.
Let’s get to a more detailed one.
First of all, you scope the project, form security management dedication, and define the budget.
Then you have to identify all the stakeholders and clearly understand all regulatory, contractual, legal, and industry requirements and standards.
After that you conduct a risk assessment and based on its results you review a set of your security controls and implement missing ones.
At the next stage, you ensure internal availability and acknowledgment of managing the project.
Now you have to prepare all necessary documentation.
You also need to conduct training for your employees and execute it also every time you hire a new specialist
After you need to develop a report in a way of e.g., risk treatment plan
Now you just continue to measure, audit, monitor, review, and so on and, of course, you take preventive actions or correct your processes if needed.

By the way...
How To Implement Zero Trust Security: Practical Steps
Give up the long-established “trust but verify” architecture of on-premise network deployments. The zero trust approach promotes and practices the “never trust, always verify” philosophy.
Read the full guideBenefits
What are the Benefits of ISO 27001?
- Protection of information
- Attack resilience raise
- Protection from ripening security threats
- Leakes and breaches prevention
- Control measures implementation
- Best security practices execution
- Established risk management
- Compliance with national and international regulations
- Improvement of overall company security
- Brand reputation enhancing and protection
- Audit requirements satisfaction
- Cost reduction from a long-term perspective
- Company culture enhancement
- Security warrant for customers
What do our C-levels say?
“We are extremely honored to, officially now, meet the ISO 27001:2013 requirements. The road was long, yet engrossing. This is proof of our reliability and expertise. This is the engraved title: “We worth it. We are trusted by one of the most trusted and powerful organizations in the world. This is a luminescent sign for our customers and partners: “You can grow here, you can grow together with Geniusee. Those guys look like they know what they’re doing”. Anyway, it does not mean this is all. We’ll continue to ameliorate our expertise. I can’t wait to get to the next stage” - Taras Tymoshchuk, CEO and co-founder of Geniusee.
Ihor Demkovych, Head of Engineering at Geniusee, was the main person responsible for implementing all required processes. He gave us a few comments on the subject.
Interviewer: "What new opportunities does ISO 9001:2015 open for the company?"
Ihor: The certificate confirms that the company has introduced information security management processes and that security controls are fully implemented. This makes it possible to prove to clients at the documentary level that we care about the security of their data. Often, tenderers are required for the availability of certificates of a similar type, which will enable Geniusee to expand sales opportunities. Also, preparation for certification helped to specify the number of processes and formalize all key stages of the processes taking place in the company.
Int.: "What was especially callous when preparing to receive a certificate?"
Ihor: In preparation for the certification audit, a project was developed to introduce management systems that would implement ISO 9001 and ISO 27001 standards. Geniusee uses integrated QMS and ISMS management systems that complement each other. Initially, documentation was developed in accordance with the requirements of the standard, and taking into account the characteristics of the company, the developed policies apply to all units of the organization and formalize the rules for the functioning of a particular office to comply with the requirements of standards. Changes have been made to Sales, Recruitment, HR, Delivery, SDO, QMO, R&D, and UI/UX offices. The most difficult thing was to implement changes that concerned all employees of the company, for example, familiarity with system management, training, or detailed documentation of the implementation of processes.

Did you know?
Geniusee Received An ISO 9001:2015 Certificate
The adoption of a QMS is a strategic decision aimed to assure our ability to provide customers with services that meet both their needs and regulatory standards.
Find out what it meansInhouse or outsource?
Now, you may be guessing, what to choose, an inhouse team to fit ISO 27001 compliance or hiring an outsourcing company that already has the certificate?
Let’s get through a comparative table.
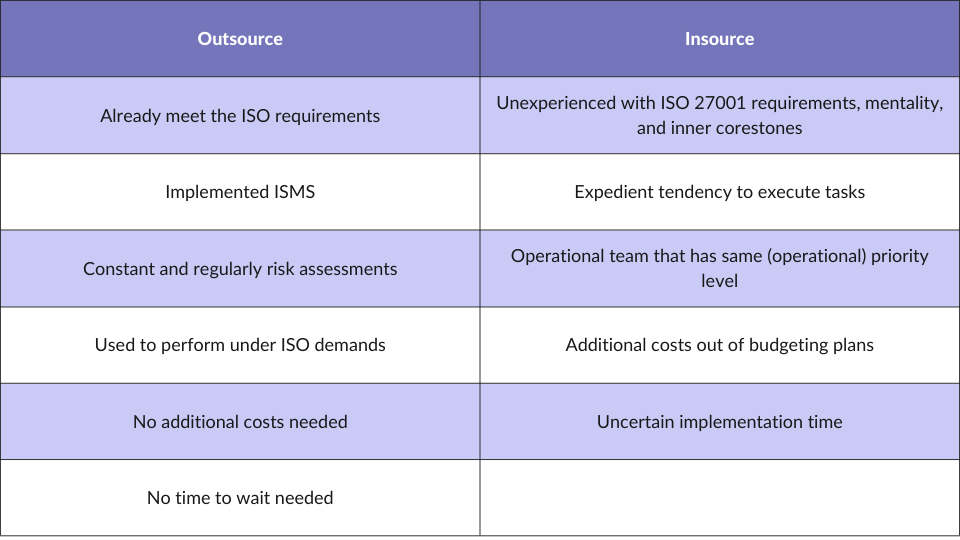
It’s only you who decides, but if you need to implement a highly-secured project now, an outsourcing company seems as the best choice. If you want to hire a team of dedicated professionals that work in the most secure possible way, call us!