The departure of top management is not just a personnel change — it's a critical juncture for data security. With high-level executives often having access to the most sensitive company information, their exit can pose significant risks.
When top management changes, it can disrupt the day-to-day operations of a company.
This disruption can create vulnerabilities in data security, leaving sensitive information exposed to potential threats. It's essential to safeguard your data during this time to prevent any breaches or data leaks that could harm your business.
In this article:
The importance of safeguarding data during top management changes
A change in top management often means a change in the personnel responsible for data security. New management may not be familiar with the company's existing security protocols, leaving room for errors or oversights.
Additionally, employees may be uncertain about their new roles and responsibilities and may overlook critical data security measures.
All of these factors can put your company's data at risk.
Safeguard your business with us!
With our cybersecurity services, you can grow your business in a trusted and resilient digital environment.
Understanding sensitive data and its vulnerabilities
Before implementing data protection measures, it's essential to understand what sensitive data is and its vulnerabilities.
Sensitive data refers to any information that, if compromised, could cause harm to an individual or business. This includes personal data, financial information, trade secrets, and confidential business information.
Sensitive data can be vulnerable to cyber-attacks, human error, and physical theft.
Cyber-attacks, such as hacking, phishing, and malware, can compromise sensitive data stored online.
Human error, such as sending an email to the wrong recipient or misplacing a device containing sensitive data, can also lead to data breaches.
Physical theft, such as stealing a laptop or hard drive, can also result in the loss of sensitive data.
Risks associated with top management changes and data security
Insider threats
Insider threats refer to the risks posed by employees with access to sensitive information.
During a change in top management, employees may become disgruntled or uncertain about their new roles and responsibilities. This uncertainty can lead to mistakes, oversights, or malicious actions that could compromise your company's data security.
Lack of oversight
There’s also may be a lack of oversight in terms of data security. New management could not be familiar with the company's existing security protocols and may not prioritize data security during the transition.
External threats
External threats, such as cyber-attacks, can increase during a change in top management. Hackers may take advantage of the disruption caused by the transition to launch attacks on your company's data.
It's important to have a plan in place to mitigate these threats and keep your data secure.


Thank you for Subscription!
Best practices for data protection during top management transitions
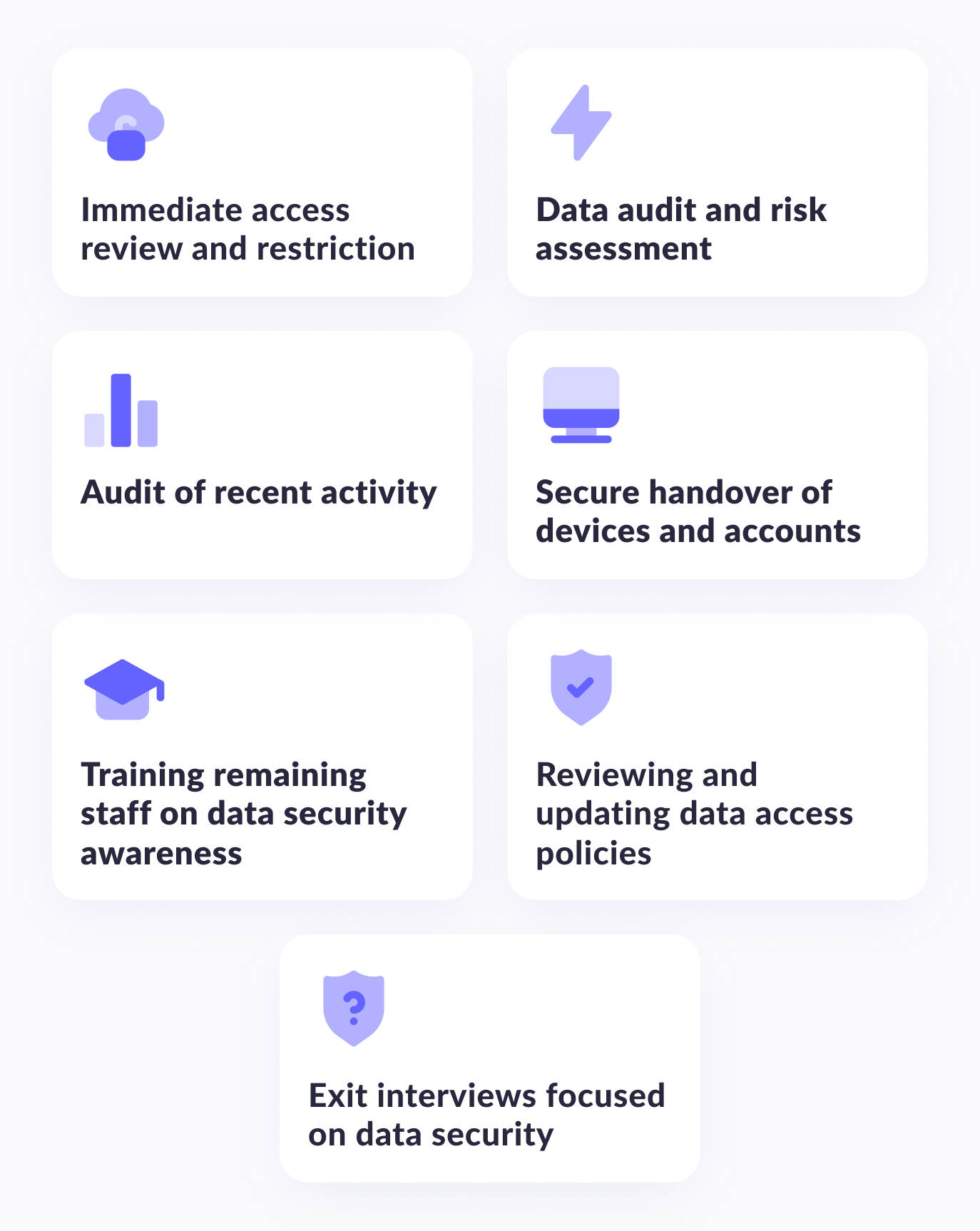
1. Immediate access review and restriction
As soon as a top executive announces their departure, conduct an immediate review of their access privileges.
This includes not just their direct access to systems and databases, but also any administrative rights they may hold.
Restricting access should be done tactfully and professionally, ensuring that the departing executive still retains the access necessary to fulfill their remaining responsibilities, but no more.
2. Data audit and risk assessment
Before you enhance data protection, it's crucial to know what data you have and where it's kept. A data audit and risk assessment can help find weaknesses and areas for improvement.
It involves listing all the data your business collects, processes, and stores, whether on servers, in the cloud, or on mobile devices.
Once you've identified the data, categorize it by sensitivity and determine its usage and access permissions.
A risk assessment involves spotting potential threats and vulnerabilities that could lead to a data breach. This includes evaluating IT infrastructure security, identifying possible attack points, and assessing the effectiveness of current security measures.
3. Audit of recent activity
Conducting a thorough audit of the departing executive's recent digital activity is crucial to ensure there are no anomalies or suspicious actions that could indicate a data breach or theft.
It’s important to look for unusual file transfers, email attachments, or access to sensitive areas in the system.
4. Secure handover of devices and accounts
Ensure a secure and complete handover of all company-owned devices, including laptops, mobile phones, and tablets.
Similarly, ensure that all accounts, especially email and cloud storage, are either transferred to a designated successor or deactivated.
5. Exit interviews focused on data security
Exit interviews should include a discussion about the confidentiality of company data.
Remind the departing executive of any ongoing obligations they have regarding the non-disclosure of sensitive information.
More on the topic
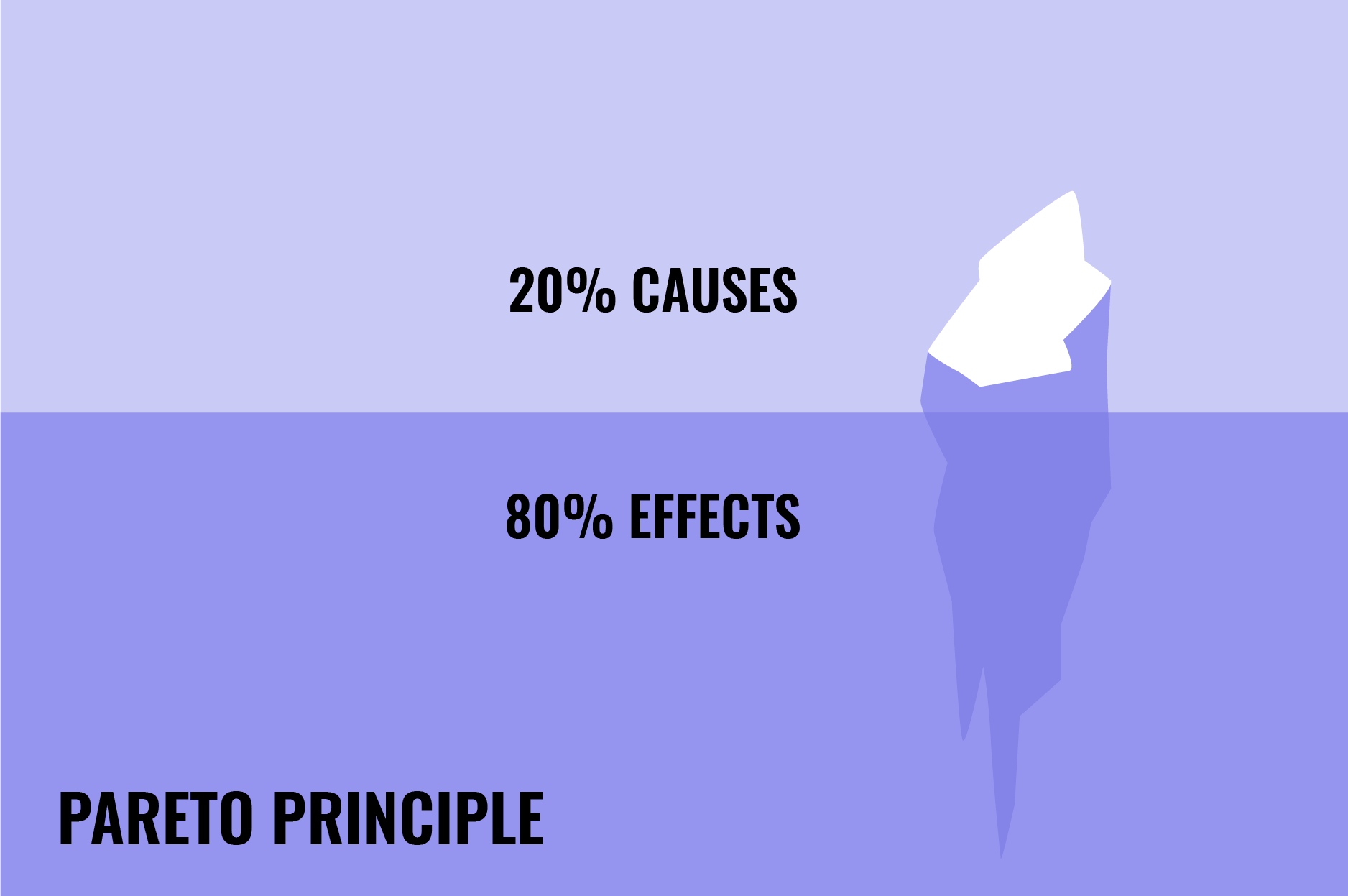
Pareto Principle In IT Security
Apply the Pareto Principle to streamline IT security by targeting the vital 20% of issues responsible for 80% of risks. Discover efficient risk mitigation strategies.
Read the whole article6. Reviewing and updating data access policies
Use this opportunity to review and, if necessary, update your company's data access policies.
This might include reassessing who has access to what data and whether current protocols are sufficient in safeguarding against unauthorized access.
7. Training remaining staff on data security awareness
Finally, reinforce the importance of data security with your remaining staff. Provide training and resources to ensure they understand the risks and their role in protecting the organization's information.
Conclusion
The departure of top management is a sensitive time for any organization, especially in terms of data security. By taking proactive steps, you can mitigate risks and maintain the integrity of your company's information.
Remember, data security is not just a technical issue — it's a cultural one that involves every member of your organization.





















