A modern-day IT team may plan proactively for several internal and external threats related to cybersecurity, data breaches, or hacking. Yet, war is not a scenario that the average IT team plans for—at least until 2022.
However, the recent events in Ukraine have brought the idea closer to home. War is now a reality, and even the information technology industry should be prepared for cybersecurity defense. As a result, your team members may ask what this means for you or what has been done to mitigate threats of any future attacks.
Let's take a closer look at the role of cyber defense in wartime and what can be done to enhance your company's cyber security in a proactive approach.
In this article:
What Is Cyber Defense, and Why Is It Necessary?
Cyber defense is your ability to shield the IT system from potential cyberattacks. With a robust cyberattack defense system, you proactively anticipate probable cyber threats in advance and prevent attacks accordingly.
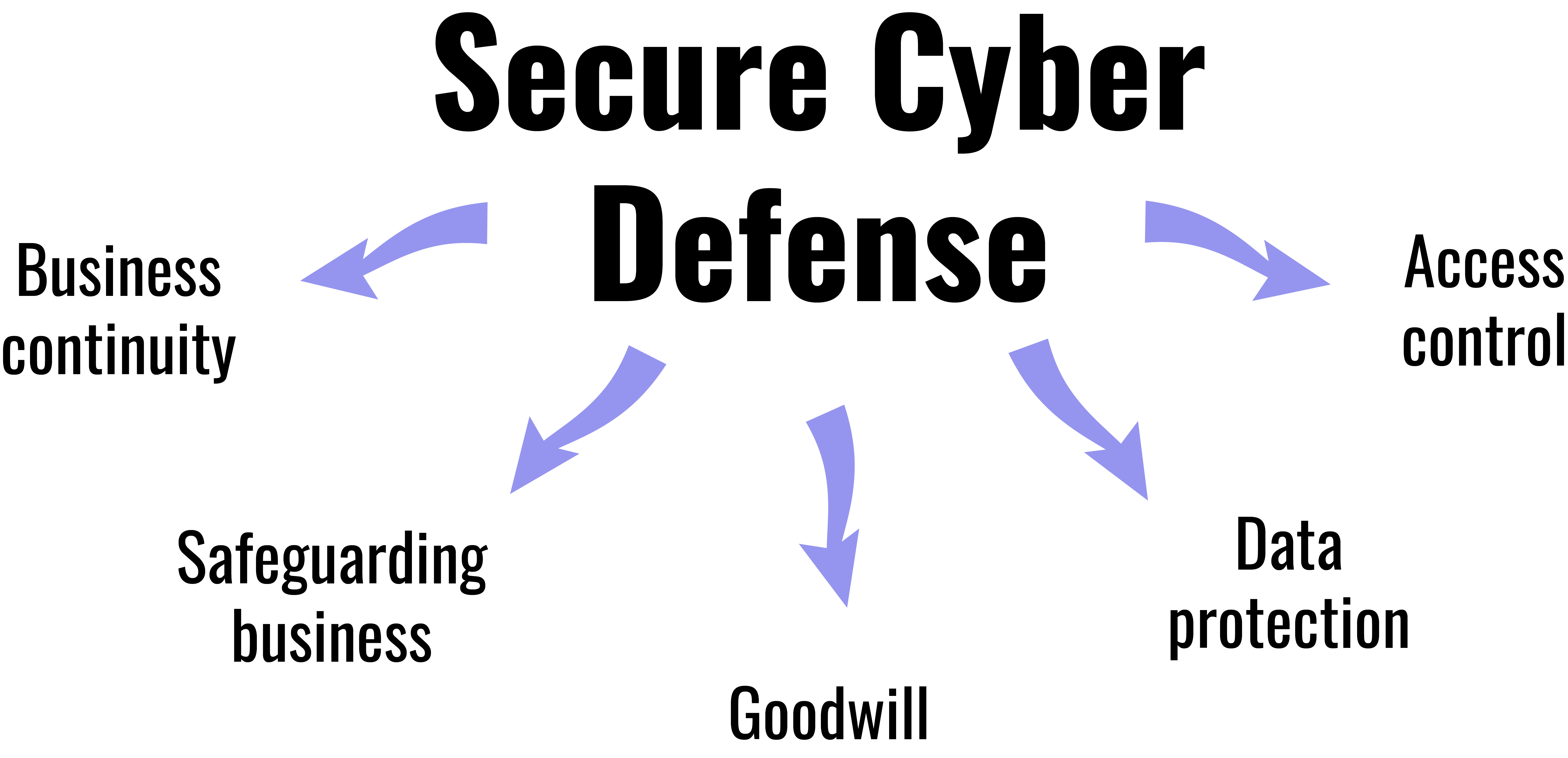
Let’s get an idea of why implementing secure cyber defense in your company, especially during wartime, is essential:
- Safeguarding business. By deploying security measures, you can keep your business safe from persistent threats and cyber attacks and remain functional during a war.
- Data protection. Losing your sensitive information will be costly. Therefore, you need to protect your network and endpoint devices from data breaches and malicious software.
- Access control. Preventing unauthorized access to your system will make it easier for you to reduce potential vulnerabilities.
- Business continuity. To keep your business functional during a war, you will have to depend on IT, mobile devices, and communication technologies. As a result, you will be more susceptible to cyberattacks.
- Goodwill. Having a solid cyber defense mechanism and security measures can win the all-important trust from your end-users and customers.
After learning the main principles of cyber defense, it’s worth mentioning threat intelligence analysis. This is a recent concept to secure your cyberspace that can be a game-changer. Here’s how.
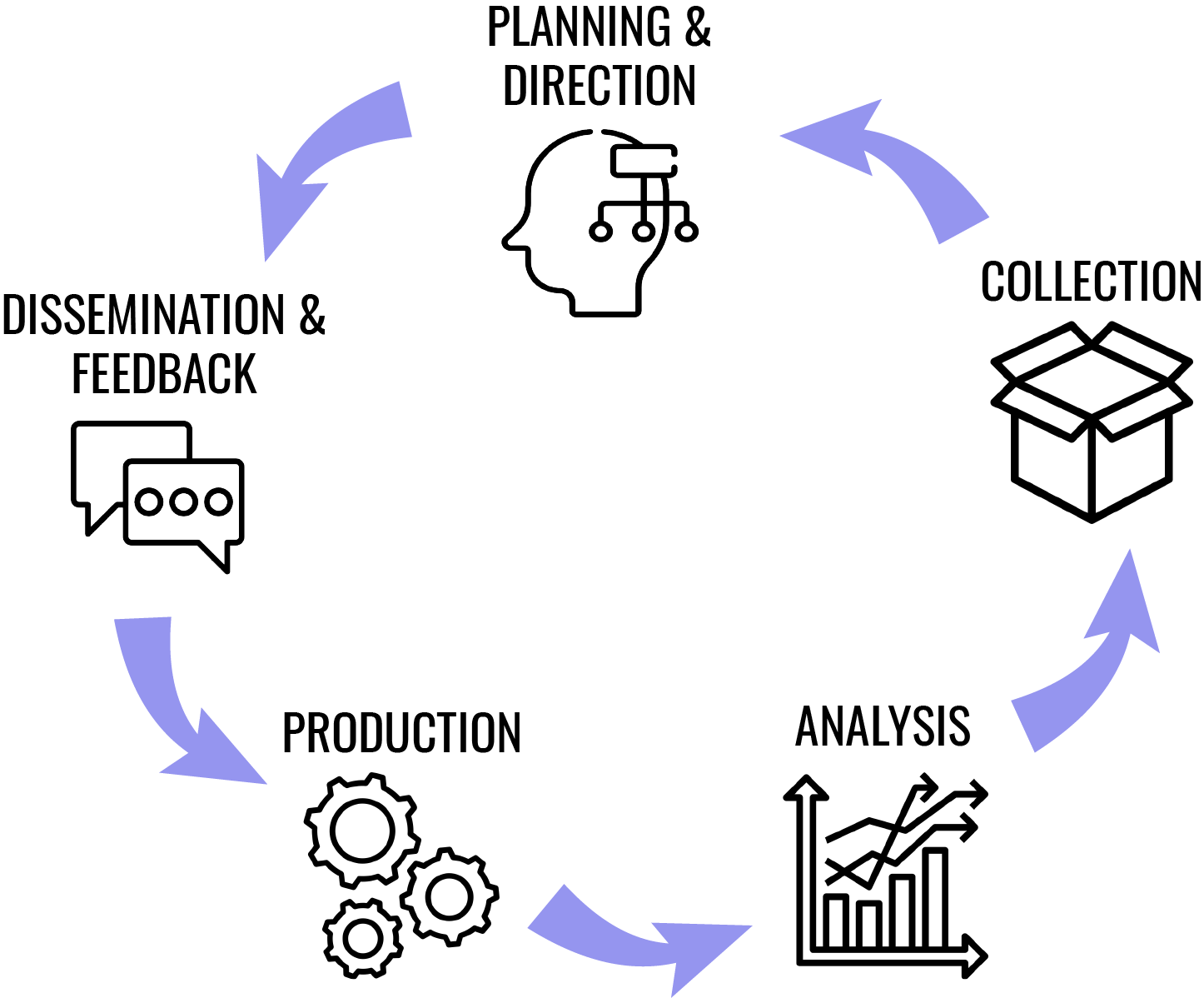
Cyber Threat Intelligence Analysis
Threat intelligence analysis lets you examine large varieties and quantities of relevant data with specialized software and hardware. This helps derive information on current and upcoming cybersecurity threats for your business and helps you with risk mitigation proactively.
However, despite its effectiveness with cyber defense, threat intelligence analysis is not something you can perform overnight. It requires a great deal of commitment, time, expertise, and effort from your IT team.
And that is easier said than done. War always comes unexpectedly, so you won’t have enough time to assemble your team and resources. An ideal technical partner will make the process smoother for you without a dedicated cybersecurity team.
When choosing your cyber defense contractors, make sure they adhere to cyber defense operations' best practices and have relevant certifications. For example, Geniusee is an ISA-certified tech support provider, meaning the ISA certification authority regulates the security and safety stands of the company.
Let’s now discuss how you can put your shields on to defend your cyberspace from wartime threat actors.
Defense Against Cyberattacks
There are two aspects of managing your cyber defense—hardware and software. Although your average IT team already has some of those systems in place, you may need some upgrades considering the wartime situation. Check out below advanced but inexpensive tools you may need.

Cybersecurity Hardware
Here are the hardware aspects first.
- Firewall with VPN protection. A VPN-enabled physical firewall can provide a much better cyber defense than your network’s software-based firewall through continuous encryption of your network and data communication.
- Security keys. Can you guess the most common password used globally? It’s the word “password” itself. Indeed, your team members use better login credentials than this. However, it remains highly vulnerable to brute-force attacks. Physical security keys use dynamic password configurations and security information to protect your system.
Apart from procuring the proper hardware, you will also need to implement the correct configuration for your software to have the reliable cyber attack defense.
Settings and Configurations
The following is an outline to enable your system and utility software with proper settings for a tighter cyber defense.
- Office 365 secure score. Use the Office 365 secure score to find out the problem areas in your network security and fine-tune accordingly.
- Multi-factor authentication (MFA). Use MFA as an additional security step to validate user logins.
- Password vault. Use a password vault to store your login credentials to avoid the hassle of remembering the complicated ones.
- Auto-updates. Enable auto-updates for your operating systems and software to always get the latest security patches.
- Malware scanner. Frequently scan your system with a dedicated malware scanner.
- Data encryption. Keep your storage fully encrypted to ensure data privacy even in the case of a loss or theft.
- Training. Take advantage of the free resources available on Youtube to train your team members about prevention and incident response.
- IP locking. On top of multi-factor authentication, lock down your IP address during host migration to add an extra layer of security. HubSpot, Pardot, and several other third-party tools have this feature.
- Backup. Perform routine backups of your system and use separate login credentials for the backup data.
These essential steps and configurations can help safeguard your system from potentially malicious cyber incidents.
Prevent Data Breaches and Protect IT Solutions
To put a robust cyber defense in place for your business, keep in mind that new threats appear daily. Take the following additional steps to mitigate your risk of data breaches:
- Educate your team members about the potential loopholes and the importance of information security.
- While partnering with businesses, make sure they also have the right cyber defense tools and policies.
- Conduct periodic vulnerability and threat assessments by third-party cyber defenders with appropriate professional expertise and security tools. For instance, Geniusee can assemble dedicated teams for your cyber defense project.
Final Thoughts
With these cyber security defense settings in place, you will better handle what is happening within your business network and external environments during wartime. In addition, an adequate cyber defense will help you anticipate threats early and make you prepared.
Still have questions? Ask the Geniusee professionals.





















