Has your company recently released an app, software, or any IT product? If so, did you ensure top-level security for it?
Hacking, through security protections in an app or software, used to require a lot of time, skill, and effort. However, the numerous technological breakthroughs that have occurred up to this point have made it quite simple to carry out application assaults that jeopardize an app or software.
Fortunately, a technique known as pen testing helps identify the weakest places in your app, software, or IT infrastructure and proactively safeguard them before someone exploits them.
What is the significance of a penetration test? According to the results of recent research performed by Core Security, 97% of respondents believe it is indispensable to their security condition.
So, let's learn in detail what pen testing is and the numerous types and ways for implementing it.
In this article:
What Is Penetration Testing?
A penetration test (or pen test) is a special assessment that attempts to evaluate the security of an IT infrastructure by exploiting its weaknesses in a safe manner. These flaws might be discovered in operating systems, services, and applications, as well as erroneous configurations and risky end-user behavior.
Pen testing is considered ethical hacking since pen testers intentionally perform cyberattacks by using penetration testing tools and strategies created to exploit websites, apps, and networks, among others.
Why Is Pen Testing Important?
After explaining its meaning, let's examine why penetration testing is necessary. For starters, it may boost an organization's security in a variety of ways. Here are a few instances of why pen testing is important.
Identify and Prioritize Security Risks
Pen testing evaluates a company's ability to defend its networks, apps, endpoints, and even people against external or internal efforts to gain unauthorized access to protected assets by bypassing security regulations.
Intelligently Manage Vulnerabilities
Penetration testing provides businesses with knowledge about genuine security flaws that might be abused. It is a quick and easy approach to find all of these flaws. As a consequence, the business will be able to deploy critical security patches and devote security resources more effectively.
Leverage a Proactive Security Approach
Despite all the technological advances, there still isn’t a single solution that can be used to prevent various security breaches. For that reason, companies must equip themselves with multiple security mechanisms and tools, including antivirus, cryptography, or even identity and access management (IAM) programs.
Even with these security solutions, however, eliminating every existing risk in an IT environment is hard. Companies utilize penetration tests to uncover all of their security problems and work proactively to remedy them.
Verify Existing Security Programs Are Working and Discover Security Strengths
Another significant advantage of penetration testing is that it reveals more than just what isn't working. These tests are also used as quality assurance checks in order for businesses to understand their effective policies and security flaws. These insights enable a business to deploy security resources strategically, ensuring they are available when and where they are most needed.
Increase Confidence in the Company’s Security Strategy
A company can never be confident in its security strategy unless it is tested. By putting the company’s security infrastructure under penetration tests, it won’t need to wonder what an attack will look like and whether it will be able to defend itself from it. With pen tests, a company will know how to prepare properly and enhance its security strategy, never to be caught off guard.
Meet Regulatory Requirements
Penetration testing aids companies in complying with the general auditing and compliance aspects of regulations and industry best practices. Penetration testers can show how a hacker could obtain access to sensitive data by attacking an organization's infrastructure. Periodic mandatory testing ensures that the company always stays one step ahead of attackers by finding and addressing security flaws.
Now that we’ve addressed all the benefits of penetration testing let’s explore the different types of pen tests.
Types of Pen Tests?
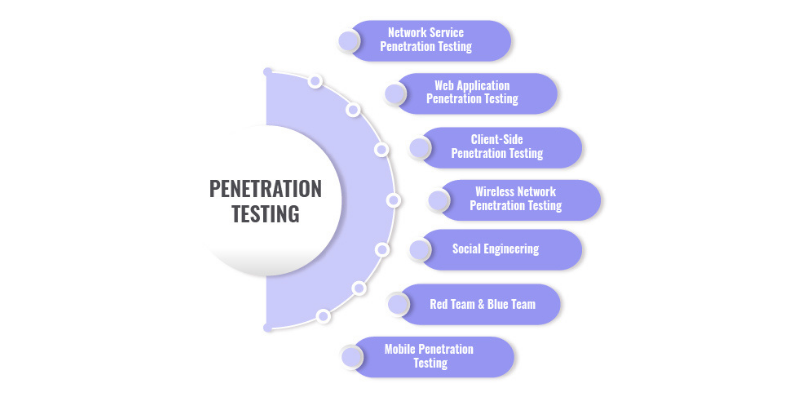
There are different types of penetration testing, including:
- Network Services
- Web Application
- Client-Side
- Wireless
- Social Engineering
- Physical Penetration Testing
To carry out each type of pen test, specific knowledge and tools are required. Now, let’s explore each of these tests in more detail.
Network Services
Network service is the most prevalent type of pen testing.
Its principal goal is to discover the most susceptible security flaws in an organization's network infrastructure (for example, servers, firewalls, switches, routers, printers, workstations, and more) before they can be exploited.
Web Application
Meant to identify security weaknesses in web-based apps, this method utilizes a variety of approaches and assaults in an attempt to obtain access to the web app itself.
Web application pen tests are very detailed and targeted. Endpoints of any web-based application that interact with the user regularly must be identified for the test to be considered successful.
Client-Side
A vulnerability assessment used to discover threats and weaknesses in client-side applications, this type of testing includes programs such as email clients, web browsers, Macromedia Flash, and even Adobe Photoshop and Microsoft Office Suite.
Wireless
This type of pen testing entails detecting and inspecting the connections between all devices linked to the company's wi-fi, such as laptops, tablets, smartphones, and other IoT devices.
Wireless pen tests are most frequently performed on-site because the testers have to be within range of the wireless signal to access it. Another option is to place a NUC and Wi-Fi Pineapple on-site for the pen testers to complete the test remotely.
Social Engineering
During this pen test, a simulated attack is carried out to try and trick the staff into revealing sensitive information, such as a login and password.
Pen testers carry out the most common attacks: phishing attacks, name-dropping, tailgating, eavesdropping, gifts, and imposter attacks.
Physical Pen Testing
This test imitates a real-world threat. The pen tester attempts to breach physical boundaries to get entrance to a company's infrastructure, systems, or people.
This test's greatest advantage is that it shows weaknesses in physical controls such as locks and cameras. This can help a company strengthen its physical security posture.
Now that you know the basics of each type of penetration testing, you may ask what its stages are.
Penetration Testing Stages
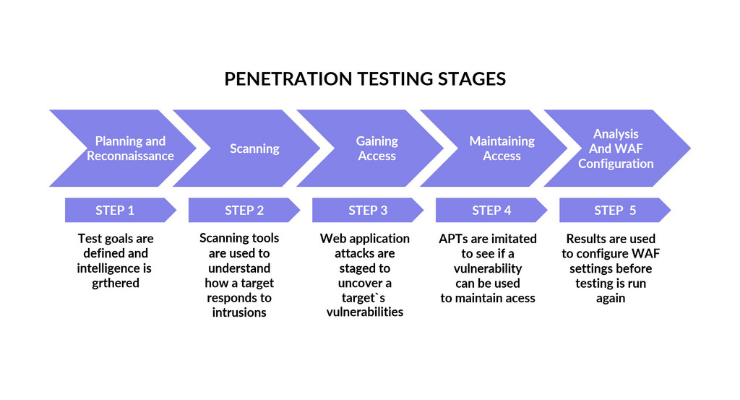
Pen testing consists of multiple stages. In this section, we explore these stages and their purpose.
- Information gathering. The first stage in the pen testing process consists of providing the pen testers with essential information regarding in-scope targets.
- Reconnaissance. During this stage, the testers try to identify additional information that the company could have overlooked or not provided for any reason. This step is of crucial importance with external testing.
- Discovery and scanning. The information gathered is used to decide whether ports and services are available for specific hosts or subdomains for web applications.
- Vulnerability assessment. This stage provides additional knowledge and allows the testers to identify likely weaknesses that could allow an attacker access to the environment or technology that is tested.
- Exploitation. During this stage, the real action happens. After interpreting the results from the vulnerability assessment, the testers proceed to attack and exploit all the vulnerabilities.
- Final analysis and review. After the attacks have been carried out, the testers put together a comprehensive report describing the testing process, the vulnerabilities discovered, and how the testers exploited them.
- Utilize the testing results. The final stage is the most important. The company should examine the test results and then list vulnerabilities and come up with remedial actions.
After discovering pen testing types, the next important step is to get familiar with its methods.
Penetration Testing Methods
 In addition to different types of pen tests, there are also different penetration testing methods. In this section, we explore them in more detail.
In addition to different types of pen tests, there are also different penetration testing methods. In this section, we explore them in more detail.
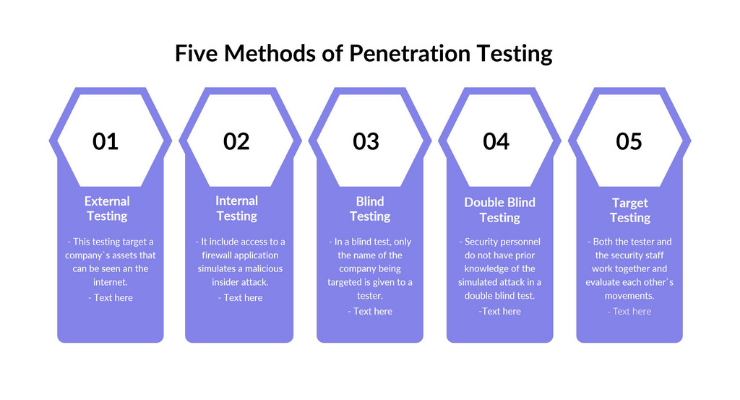
- External testing. External penetration tests target a company's assets that are visible on the internet, such as the web application itself, the company website, and email and domain name servers (DNS). The purpose of this testing method is for the tester to access and extract meaningful information.
- Internal testing. Penetration testers with access to a program behind its firewall imitate an attack during internal testing. Engaging with an employee whose personal information was taken as a result of a phishing attempt is a popular testing scenario for this strategy.
- Blind testing. When a blind testing method is carried out, ethical hackers are provided only with the company’s name. This gives the company and its employees insight into what an attack would look like and the potential consequences.
- Double-blind testing. When double-blind testing is carried out, employees in charge of security are not informed in advance that a simulated attack will take place. This way, they won’t have any time to prepare their defenses before an attempted breach, just like an actual attack.
- Targeted testing. With the targeted testing approach, both the security professionals and the pen tester collaborate and keep each other informed of their whereabouts. This approach is a fantastic training exercise that delivers feedback from the perspective of a hacker to the company's security staff.
Now that we’ve explored the different pen testing methods, let’s focus on different security issues these tests can reveal as well as how to avoid them.
Security Issues: How to Avoid Them
Every security threat can be repealed and prevented with a proper approach. The most popular attack and their precautions are:
DDoS
A distributed denial-of-service (DDoS) attack is an attempt to disrupt regular traffic to a targeted server, service, or network by flooding the target or its encompassing infrastructure with traffic.
There are three ways to prevent DDoS attacks:
- Black hole routing. This solution includes the creation of a black hole route and funneling all the traffic into that route. If an internet property is under a DDoS attack, the ISP provider can send all the traffic into the black hole as a defense.
- Rate limiting. Limiting the number of requests a server will take over a specific time period is another method of preventing DDoS attacks. However, this method will only slow down the attackers from stealing content or prevent brute-force login attempts. But, rate limiting is unlikely to prevent a complex DDoS attack.
- Web application firewall. Putting a web application firewall (WAF) between the internet and an origin server will cause the WAF to act as a reverse proxy and protect the server from malicious traffic.
Now that it’s clear how to stay safe in case of a DDoS threat, let’s check out another widespread attack.
SQL Injection
SQL injection is a typical attack vector that employs malicious SQL code to manipulate backend databases in order to gain access to information that was not intended to be displayed. This type of attack may result in unauthorized access of user lists, deletion of whole tables, and, in certain situations, the attacker acquiring administrator rights to a database, all of which are extremely damaging to a corporation.
SQL injection can be prevented by:
- Not putting data into the database without processing.
- Not putting control structures and identifiers entered by the user into the request.
Yes, it’s that simple to save yourself from SQL injection, but often, people forget to utilize these easy and necessary procedures. Now, let’s move on to the third most popular attack.
Cross-Site Scripting (XSS)
This is a thread aimed at application users. It can be used to gain access to user accounts or alter page content in order to deceive app users or deface a website.
There are several ways to prevent XSS attacks:
- Filter inputs. You should filter user inputs very strictly based on expected or valid input.
- Encode output data. You should encode the users' output in HTTP responses to protect their data from being stolen. This can be done by combining HTML, URL, JavaScript, and CSS encoding depending on the output context.
- Use the correct response headers. You should use the Content-Type and X-Content-Type-Options headers to prevent responses containing JavaScript or HTML. They ensure that responses will be interpreted in the way you want.
- Use Content Security Policy (CSP). You should use CSP to reduce the severity of any XSS attacks that may happen.
Being fully armed against attacks, you may have a question about pen testing tools.
Penetration Testing Tools
Carrying out pen testing is easily done with the help of specialized tools. Here are the most popular and efficient pen testing tools currently available.
Netsparker Security Scanner
The Netsparker Security Scanner is a web-based and on-prem pen testing tool that can automatically search for multiple security threats on a website.
Key features:
- Scans 1000+ web applications simultaneously
- Automatic scanning
- Allows adding multiple team members
- Proof-based scanning
- API scanning
- Own JavaScript engine to scan websites
- Automates scheduled future scans
- Built-in reporting tools
Acunetix Vulnerability Scanner
The Acunetix scanner is used to search for vulnerabilities in IT systems during penetration testing. This tool is available for Windows, macOS, and Linux.
Key features:
- Scrutinize APIs and web services
- A fast scanning performance
- A low false-positive rate
- Configuration and cross-infection checking
- Network security scanning
- Integrations for CI/CD platforms
- Coordination with issue trackers
Intruder Automated Penetration Testing
This tool is also a vulnerability scanner. But, instead of IT systems, it is used to search for cybersecurity threats on a website.
Key features:
- Scans for SQL injection and cross-site scripting
- Checks common security issues in cloud environments
- Monitors public and private servers
- Provides in-depth network view
- API integration with your CI/CD pipeline
- Smart recon feature
- Regular quality PDF reporting
Pen testing tools are efficient instruments to prevent possible future attacks. You should decide on the features of each tool that are suitable for your business, or you can try all of them if necessary.
Conclusion
Penetration testing or pen testing is a simulated cyber attack against an IT infrastructure that aims to search for any exploitable vulnerabilities.
With cyberattacks becoming more sophisticated and on the increase, it is more vital than ever for companies to do regular penetration testing to detect their vulnerabilities, block holes, and verify that cyber controls are functioning properly. These tests enable the business to take a proactive attitude by identifying flaws in its infrastructure (hardware), applications (software), and people in order to establish effective controls that are ongoing and capable of keeping up with the ever-changing cyber threat scenario.
We hope this article has helped you discover what pen testing is, how the test process is carried out, and what can be done to increase the security of IT infrastructures in your company.